It’s Friday afternoon. You’ve got 3 hours left in the day before you head out for the weekend. Everyone just wants the day to be over, including you.
Suddenly, you get an email in your inbox: a new Microsoft exploit just dropped and they’re recommending everyone change their password right away.
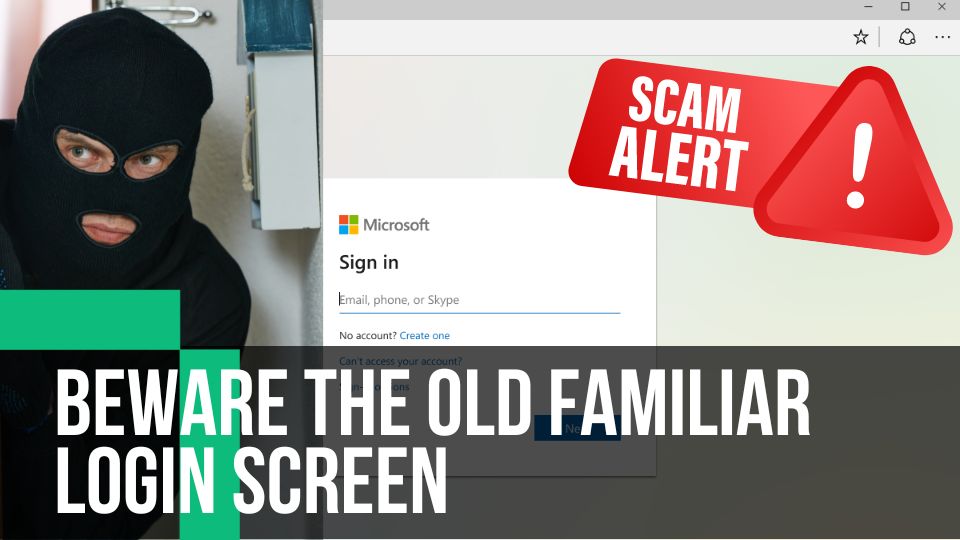
You diligently click the link. The old familiar Microsoft 365 login screen appears.
You enter your credentials.
Suddenly, you get an alert from IT. “Someone just logged into your account from Mainland China.”
“Oh, no . . .” you think to yourself as beads of sweat begin to appear on your forehead.
In our chaotic digital landscape, Microsoft has won a dubious honor: the brand most likely to be impersonated in a phishing scam. A staggering 29% of all brand impersonations in the phishing universe sport the Microsoft banner. Google and Apple follow behind, with 19.5% and 5.2% respectively1.
“But wait”, you might say. “I run a savvy ship. My crew knows an imposter when they see one.” Here’s the wrinkle: cyber crooks are masters of disguise. They’ve made a meticulous study of the Microsoft brand, right down to the fonts and colors. It’s a high-definition mirage.
Let’s not mince words. The status quo isn’t a lapse in Microsoft’s judgment; they’re not the ones sending you these Trojan horse emails. It’s a reflection of the ever-adaptive methods of cyber tricksters. What they lack in originality, they make up for in execution. They are less likely to change their tactics, because, quite simply, these tactics work.
And now, with the power of AI, the quality of phishing emails makes them all but indistinguishable from the real thing.
The rabbit hole gets deeper. One of the latest hoodwinks tells you there’s been “unusual activity” on your Microsoft account. The instinctive part of you wants to click. To act. But that’s exactly what they want. These baits aren’t simply annoying disturbances; they’re locked and loaded traps, aimed to swipe everything from login keys to your MasterCard digits.
And let’s not forget the shift in target industries. Financial services like Wells Fargo and e-commerce moguls like Amazon also share the limelight, rounding up the top five with 4.2% and 4% respectively1.

Reality Check: The Defense Plan
Now, you’re not helpless. Your sword and shield in this labyrinth of deception is a strategy as ancient as time but as effective as ever: vigilance. Slow down. Observe. Analyze. When an email claims to be from Microsoft, don’t just skim, scan. And remember, like the bank, Microsoft will never, ever ask you to reset your password.
The telltale signs are often glaring: misplaced logos, slight discrepancies in the domain names, typos sprinkled through the text like landmines. Being observant isn’t a chore; it’s a necessity. It’s how you distinguish the real from the replica. Your first line of defense isn’t a firewall; it’s a trained eye.
Bottom line? Our fast-paced digital age isn’t just about riding the big waves; it’s about navigating the undertow. While technology might be our lifeline, it’s also a landscape ripe for illusion. The challenge, then, is not just in embracing the familiar but in scrutinizing it.
In an era overflowing with technological advancements, this might seem like a back-to-basics approach. And yet, it could be the most forward-thinking thing you do.
Questions? Need to fortify your defenses? Let’s talk.