Phishing: Whether your knowledge of the subject amounts to the special at the local seafood joint or you fancy yourself a tech-savvy business owner, you must be aware of the implications behind email-driven threats.
if you don’t know what a phishing email is, think of it like this: Imagine an innocent-looking email from a vendor, a partner or even a client. But underneath, there’s a sinister secret. The document that’s attached to that email – often disguised as a OneDrive / SharePoint link, is really a phishing page, designed to steal your Microsoft login credentials – or worse.
What’s worse? Even multifactor authentication won’t stop some of these attacks.
That’s right – once you click the link, it’s check mate – the attacker can log into your own account (and start using that to send out even more phishing emails to other unsuspecting victims – or start hunting for your valuables).
However, not all is lost. Knowing what to look for is the best defense. Take a look at these three themes we’ve gathered over the last year:
Major Threats
The most common scam by far is finance-related. Fake invoices, late payment notices and requests for confirmation make up the bulk of these sneaky scams – up to a whopping 54%. These messages are designed to prey on unsuspecting business owners – after all, not wanting to upset your key suppliers or telephone provider is a normal feeling for most of us!
Be especially careful when you receive any kind of notice with a suspicious link – as threat actors often disguise these links to prevent your malware scanner from seeing them.
What’s more, emails coming from a known source aren’t exactly safe – we’ve seen plenty of cases where the actual email of a legitimate sender was compromised. Take for example this recent email we received:
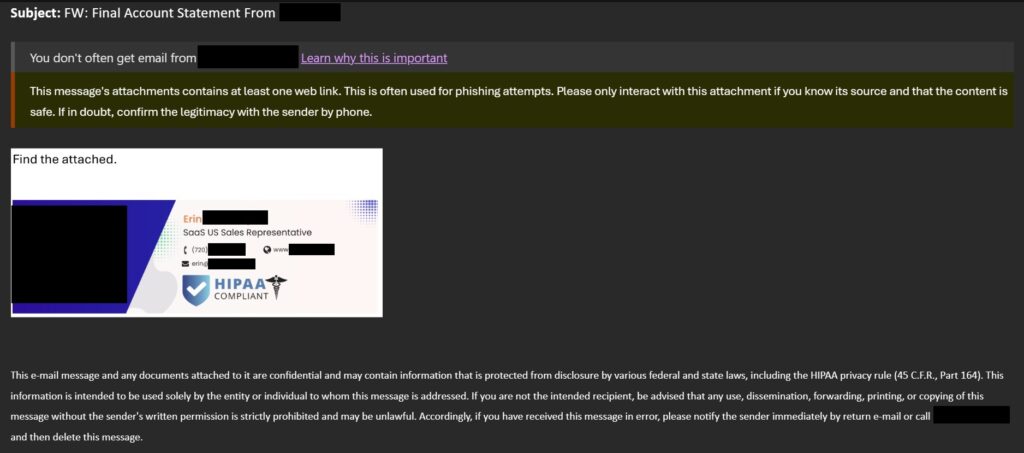
As you can see, the attackers not only compromised the legitimate email of an account manager at a company we do business with (I know what you’re thinking! Don’t worry – it’s a vendor who provides external services not related to our client operations), but they used it to try and trick their customers as well.
Not only is it out of character for them to include a separate link to download an attachment; in addition our custom Exchange rules triggered a warning as well (we actually use a clever rule to detect this behavior, hence the yellow banner at the top). We only received confirmation afterward when the company confirmed in a follow-up that the account had been compromised.
Further, be especially vigilant of emails claiming your password is expiring or other similar “high urgency” items. These nasty notifications make up nearly 35% of known attacks, and are designed to prey on your fears, plying you to take action lest you find yourself locked out or lose access to an important service.
Moderate Menaces
Shared documents and voicemails claim the podium here, making up 38% and 25% of the threats. These clever techniques utilize false information massaged in such a way as to deceive you into clicking on an infected attachment or credential-harvesting link. Don’t fall for it!
Minor Perils
While seen less often, emails involving taxes, health benefits, job applications or utilities are still common enough you should consider them a threat.
So what are the consequences of clicking on a phishing email? The consequences are dire, including monetary losses, data compromise, and identity theft. What’s worse, these attacks can impact your customers – and by extension, your business’s reputation.
Educating your staff is not an option – you must train everyone about the risks of phishing. In addition, every business needs to have strong cyber security defenses to protect against worst case scenarios – see the warning notification in our screenshot as an example, and account compromise monitoring as a more drastic “last mile” defense mechanism.
All that said, being aware of the dangers of phishing is still your best defense. By keeping informed, providing regular training and following cyber security best practices, you can rest assured that even if someone does click on a bad link, you can quickly isolate the incident and protect your digital assets.
At Leap Cloud Solutions, we protect businesses like yours by implementing industry-leading cyber security solutions. If you’re anything less than 100% certain your business is not at risk, then let’s talk.



